User access control (UAC) is a crucial component of present-time cybersecurity that makes sure that only systems or people with permission access sensitive data. Effective UAC measures must be put in place by enterprises to safeguard their assets, whether they be trading secrets, human information, or financial data. UAC serves as a proactive protection against cyber risks by controlling permissions and confirming identities, and it encourages responsibility by keeping thorough access records.
The five key techniques for efficient user access control will be discussed in this blog, which will help you improve the security posture of your company and protect important information.
Understanding User Access Control
All businesses have information that has to be protected, including financial records, personnel data, and trade secrets. User access control is responsible for monitoring who has access to this data and what they can do with it.
UAC's structure and operation might differ from business to business. From a tiered system that requires several approvals for data access to a single administrator who grants authorization, it can take many forms. Adapting your UAC system to your business's requirements is the goal.
Working of User Access Control
The foundations of UAC are permissions management and identity verification. The UAC confirms the identity of the requestor and compares it to an access list whenever a system or individual makes a resource access request. The user's access rights are determined by the permissions assigned to that identity, which are reviewed by the UAC if the identity matches an entry.
Importance of User Access Control
In this connected age, a strong UAC is essential. ERP data security is crucial given the abundance of cyberthreats. Unauthorized access is made harder by UAC, which offers a proactive way to reduce these risks.
In addition to prevention, user access control promotes accountability. It provides a record in the case of a security breach by keeping track of who has access to what, when, and how. Because of its ability to trace the origin of an issue, UAC is a crucial component of any cybersecurity plan.
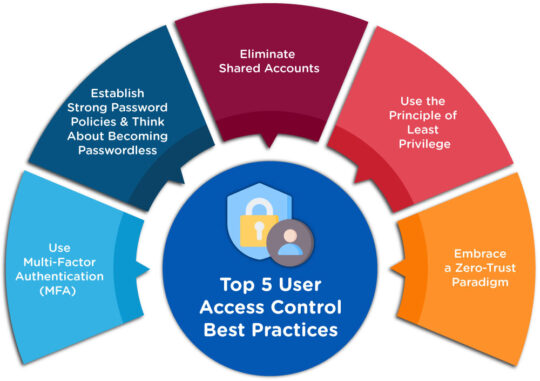
Top 5 User Access Control Best Practices
#1 Use Multi-Factor Authentication (MFA)
Users who want to access an asset that uses MFA must supply two or more verification factors. These might be something individuals own (like a smart card), know (like a password), or are (like a fingerprint).
You add an additional layer of security by putting MFA into practice. A harmful person cannot obtain access without the other requirements, even if they are successful in obtaining one. When defending against phishing attempts, which deceive users into disclosing their passwords, MFA is very helpful.
#2 Establish Strong Password Policies and Think About Becoming Passwordless
The first line of protection in security is often a password. Attackers can, however, quickly figure out or break weak passwords. Putting in place robust password policies is essential. The use of lengthy, complicated passwords and frequent password changes need to be mandated by these regulations.
Even secure passwords, however, have their limitations. They may be misplaced, pilfered, or guessed. Many firms are now thinking about adopting passwordless because of this. The danger of password-related breaches is decreased by passwordless authentication techniques like social login, magic links, and biometrics, which completely do away with the necessity for passwords. Being Passwordless is the best user access control practice.
#3 Eliminate Shared Accounts
Shared accounts are frequently a serious security issue as they are utilized by several people or systems. They hinder the ability to monitor user behavior and hold people responsible for their conduct. If something goes wrong, it's often hard to identify the culprit.
You might choose to utilize individual user accounts instead of pooled ones. To make it simpler to monitor activity and spot any possible problems, these accounts have to be linked to a particular person. Because users are aware that their actions might be linked to them, this also serves to give them a sense of responsibility.
#4 Use the Principle of Least Privilege
A user is granted the bare minimum of access required to carry out his duties under the computer security concept known as the principle of least privilege (PoLP). This user access control strategy reduces the possibility of harmful activity since it limits access to systems and sensitive data.
Putting minimum benefit into practice is an ongoing procedure. An extensive examination of users' access benefits is the first step. Upon completion of the audit, superfluous rights are terminated. Regular evaluations and adjustments are then conducted to make sure the benefits continue to correspond with the roles and responsibilities of the personnel.
Applying the concept of least privilege alone is insufficient. Additionally, keep an eye out for privilege creep, which happens when people gradually get more access privileges than they require to carry out their duties. This may be avoided with proactive management and routine audits.
#5 Embrace a Zero-Trust Paradigm
The security concept known as "zero trust" is predicated on the notion that businesses shouldn't have blind faith in everything that occurs within or outside of their borders. Instead, they should check anything that is attempting to connect to their systems before allowing access.
To implement zero trust, one must change one's perspective. It necessitates letting go of the outdated notion that the network is secure. But with the correct strategy and resources, it may greatly improve the security posture of your company.
Strengthening Security with Smart Access Control Practices!
At present, cybercrimes are at their peak, which is why it is imperative to develop robust user access control procedures. Businesses may create a strong security framework by supporting the zero-trust paradigm, implementing the concept of least privilege, removing shared accounts, implementing multi-factor authentication, and enforcing strong password regulations.
These procedures not only reduce risks but also promote a vigilant and accountable culture. It takes constant work to protect sensitive data, but your company can successfully handle the difficulties of the digital world if it has the appropriate plans in place.
Secure your business today, implement these UAC practices to stay one step ahead of cyber threats! Dive deeper into cybersecurity and beyond, visit us for more at WisdomPlexus.
Also Read: 10 Real user monitoring tools: You need to be aware about