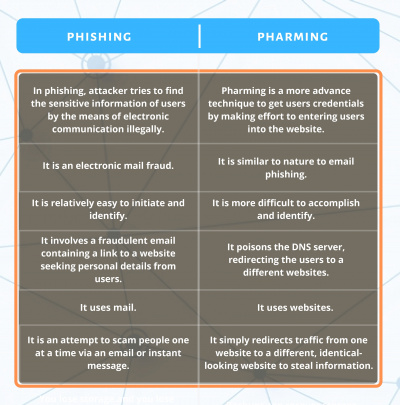
In this article, we are going to discuss Phishing vs Pharming. Phishing and Pharming are different types of cyberattacks. Criminals use these two online scams to disclose confidential information via networks.
In cyberspace, Organizations consider these two threats as the biggest threats. And as we improve the security systems of cyberspace, scammers change their tactics to scam break this security. Attackers use Phishing and Pharming for the same purpose to collect sensitive data but both of them have some differences between them.
Phishing vs Pharming. How to protect yourself from online scams?
What is Phishing?
Phishing is a cyberattack in which a malicious file or link is sent to the victim. And once the user clicks on the link or installs the malicious file, the sensitive information is disclosed to the spammer. Phishing is a type of social engineering. Attackers use Phishing with other cyber threats like network attacks and code injection.
The attacker performs Phishing attacks mostly on computer devices. In other words, Phishing is an illegal way to acquire secure and confidential information from users. One of the common examples of phishing is bank fraud, scammers act as bank employees to gather bank details of the user in a fraudulent manner.
Working on Phishing attacks
A scammer sends a message to the user. The scammer sends this message via email, social media, or other electronic communication mediums. These messages contain malicious links or files. To make this message sound genuine to the user gather basic information of the victim like name, email address, and recent activities. Spammer creates a fake message that looks genuine with all the information.
We can identify some of the attacks by observing the changes in the logo and layout of the website or pages. But still, many cybercriminals are able to create a replica of genuine web pages.
Types of phishing attacks
Cybercriminals are using several platforms and ways to disclose sensitive pieces of information from users. Here are some of the types of phishing attacks cybercriminals use.
Email Phishing
The majority of phishing attacks are sent via email. We all receive plenty of spam emails every day. With the help of fake domain names, attackers send requests or malicious links and contents to users.
To create fake domains, attackers just need to add some letters between the original domain. For instance, If the XYZ bank has a domain xyzbank.com, the attacker will create domains like xyz-bank.com, xyzbank.host.com, etc.
For users to click on the malicious links quickly without reading the whole email, attackers create the message with warnings and threats. The main purpose of a phishing email is to install malware on a user’s device, or a link is provided to a fake website where the user can submit personal data.
Spear Phishing
Spear Phishing is similar to Email Phishing but here Attackers send the malicious email to a specific audience. If the attacker is having the personal information of a user like a name, job title, email address, specific information about their job and contact information, etc then a Spear Phishing email is sent to the particular user. These are effective emails and can manipulate users to get spammed.
Whaling
Whaling is one of the popular cyberattacks today. Attackers targets employees with higher designation or senior employees. The main reason behind targeting senior management is that they have a lot of personal data in public domains.
In Whaling the attackers do not use malicious links or infected files to attack victims. Instead, they send a highly professional message with the help of the information gathered of the victim.
Smishing and Vishing
Smishing and Vishing are attacks that take place via phone instead of email. In Smishing, the attacker sends a fraud message to the user, while in Vishing attackers carry out a fraud phone conversation.
The call or message can be regarding anything like a bank account, credit card, etc to collect bank details. Sometimes Spammers use an automated call to fraud people where they type their account information.
How to Identify the Phishing Attack
Threat or Urgency type of content
You might have seen some emails with some threats content or with some sense of urgency. People click on the given malicious links in a hurry when the message encourages them to act immediately. Phishers think that if the victim reads the mail in a hurry then the victim cannot discover the inconsistency in the mail.
Format of the Message
Sometimes the format of the email is not formal or written in some irregular tone or language. For instance, if a close friend uses formal language in the email or some guy from work sends casual mail, this can trigger suspicion. The recipient must check the mail thoroughly before clicking on any links or downloading any file.
Linguistic Errors
If there is some spelling mistake in a sentence or some grammatical mistake it is a clear sign that the email is suspicious. Many organizations use spell-checking and other apps to write the content of the mail so there are no chances of having errors in genuine mails. Therefore, these emails can also count as phishing emails.
Irregular Email Addresses
Check the email address of the source first. Phishers use a mismatched email address to attack the victim. For instance, if the Bank of America is having the email address BankOfAmerica.com. Then we consider other emails address alternatives that are similar to genuine ones as spam. So check the email address, domain name, links thoroughly before clicking on any links.
What is Pharming?
A Pharming attack is a cyberattack in which cybercriminals use a fake website that almost looks similar to the real one to dispose user's login credentials like username and password. Unlike phishing where attackers send spam emails to users, Pharming is a modern way to attack a victim by sending a malicious file on the victim's computer or server that can open fraudulent websites.
Working of Pharming attacks
Cybercriminals exploit the DNS server. DNS server converts the domain name into an IP address. Organizations place DNS servers on their networks. Therefore, it is difficult to attack. There are two ways to attack the victim’s computer.
- The first way is by sending a malicious virus-infected file via email. This malicious file is installed in the system changes the host's file of the computer. If the host file is changed the network traffic is then directed away from the intended target towards the fake site. If the user types the correct web address, the host which is manipulated will redirect you to the fake address.
- Another way is by manipulating the DNS. It is also known as DNS poisoning. The DNS consists of multiple IP address tables for a particular server. If the attackers change the DNS table of a server, then the users working on that server will redirect to the fraudulent websites instead of the genuine ones. Attackers collect personal information, bank details, username, passwords, etc from these fake websites.
Measures to protect from pharming attack
- Make sure that you are working on a secure web address, HTTPS is a secure web address.
- Choosing the right and verified ISP is very important to avoid Pharming attacks.
- Install security system software into the system that can protect your DNS, and from entering into malicious websites.
- Before clicking on any links or downloading any files verify whether they are from unknown sources or not.
- Frequently change the router's passwords and WAP’s password.
- Avoid browsing fake and malicious websites.
Phishing vs Pharming. Difference Between.
Conclusion
Cyberattacks like phishing and pharming are becoming more complex and difficult to identify. An organization can face high risk and damage if attacked by cybercriminals. To avoid these attacks organizations should increase security on their network and email domains.
Another way to avoid cyberattacks is to educate the employees on the measures that must be followed to avoid being a victim of cyberattacks. Follow the safety measures thoroughly, and check and verify links and files before clicking and installing them.
You may also like to Read:
How to Recognize and Prevent Phishing Attempts
Understanding Phishing Attack – Meaning, 12 Types, and Prevention Techniques