Businesses are very much prone to attacks as they consist of plenty of data.
Such data can be financial as well as personal.
Plenty of networks are installed in order to protect the business from any attacks.
With the modern business taking an online approach it becomes more of a priority to safeguard it from any attacks.
Thus the need for auditing arises.
Let us discuss some of the questions related to network security audits.
Network auditing can be explained as the measures taken to gather the data related to the network in order to verify its functioning in accordance with the organizations requirements.
Network audit mainly involves examining the present network scenarios in compliance with the internal as well as the external policies of any organizations.
Within a network audit proper scanning of existing network architecture is done to detect any deficiencies that might put customers at risk.
Within a network audit report presence of below mentioned points are necessary:
- Analysis of security measures done.
- Any risk assessments.
- Current policies and procedures are being implemented.
- Current techniques and technology used to safeguard networks.
- Review of firewalls present.
Also Read: Top 10 Security Threats to E-Commerce to Look for in 2021
Below mentioned are some of the best network security audit tools:
Network Configuration Manager
Network configuration manager by Solar winds assists user’s in automating their network compliance procedures.
Key Features:
- Assists users in auditing their networks through a centralized platform. Users can even track multiple devices.
- Users can track any unauthorized configuration changes.
- Auditing tasks can be automated.
Network Performance Monitoring
Network performance monitoring by ManageEngine assists user in detecting any configuration violations in real time.
Key Features:
- Users will be able to monitor end-to-end network infrastructures including the local devices.
- Users receive updates about any faults through graphics as well as reports to have in depth details of it.
- Monitor the health of your network in real-time.
Network Assessment
Network assessment by Itarian assists user to perform in-depth scans to identify vulnerabilities present the network.
Key Features:
- It is easy to set up.
- Assists users with in-depth scanning for finding vulnerabilities.
- Auto report generation for scanned networks.
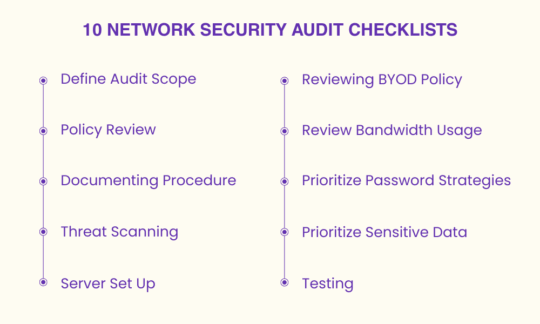
Some of the key checklists that every user needs to follow are as under:
Users, first of all, have to identify both managed as well as unmanaged devices in order to define the scope of an audit.
Managed devices would be the ones that are used and belong to the organization.
Unmanaged devices would be the ones that are not owned by the organizations and belong to visitors.
Once endpoints are recognized, a parameter is to be set up by the user.
This parameter will define the type of device that is safe for the organizations and will also recognize the ones that are dangerous for the organizations.
Check the policies being implemented within the organizations. Some of the policies are mentioned as below:
- Internet access policy.
- Bring your own device policy.
- Network security policy.
Whatever the audit process is being done, it needs to be documented in order to use it for future references.
Moreover, this process will assist in understanding the faults that a company faces in their interaction with networks.
Having knowledge of what we are protecting our networks from makes it easier to assess our system functioning.
Some of the threats that users need to secure their parameters from are as malwares, BYOD, physical breaches etc.
Server set-up or server provisioning means setting up servers based on usage which is dependent on required resources.
Some of the checklists that need to be done to secure servers from threats are network Configuration, Patching, Anti-virus usage, Domain Joined etc.
Many of your employees are going to use their devices. This can be a potential risk for the networks as these devices are not registered with your network.
However, users can set up certain policies wherein the use of such devices is given minimum access to ensure safety of the network and files stored on it.
By reviewing BYOD policies users will be able to evaluate the devices that have connected with the network and the vulnerabilities the network will have with such devices.
Bandwidth is not always unlimited.
Its usage patterns can assist users in understanding whether there is a need of expanding the network or not.
Moreover, with the knowledge of how much bandwidth is getting used, users will be able to prioritize their applications.
Make sure that your employees are using stronger passwords.
Two-factor authentication can prove very useful in such scenarios.
Moreover, it will be better if different passwords are being used for different accounts.
Data is the backbone of your organization.
Users should limit the access of sensitive data.
Allow access of sensitive data to only those who are authorized to perform tasks on it.
The limited access that users will give to such data the more chances are there that it can be kept safer.
To find vulnerabilities in your network keep testing your network.
One of the methods that is commonly used in such a process is penetration testing.
Penetration testing will assist users in finding any vulnerabilities in the network.
Static penetration testing will check the code when the program is not running.
Dynamic testing will check the code while the program is running.
Conclusion
Network audit has to be done almost on a regular basis. However, audit procedures differ from one organization to another. Above mentioned network audit checklist will assist users in auditing their network accurately.
Also Read: List of 8 Network Segmentation Security Best Practices: You need to be aware about