In cybersecurity, vulnerability assessment (VA) is an essential procedure that requires locating, categorizing, and ranking security flaws in computer networks, applications, and systems. This aids organizations in reducing possible risks before such threats may be used against them.
In this reading journey, you will understand the meaning, 5 best tools, and techniques of VA. Let’s dive in!
What is a Vulnerability Assessment?
Finding dangers or flaws in computer systems, networks, and software, as well as the risks they entail, is the process of VA.
By using black box or grey box security testing, vulnerability assessments replicate actual hacker attack scenarios on apps. From a hacker's point of view, every program is a "black box," and they just use advanced scanners to brute force different kinds of attacks.
Vulnerability Assessment (VA) and Penetration Testing (VAPT) assist companies in identifying potential risk areas and prioritizing remedies according to severity.
5 Best VA Tools
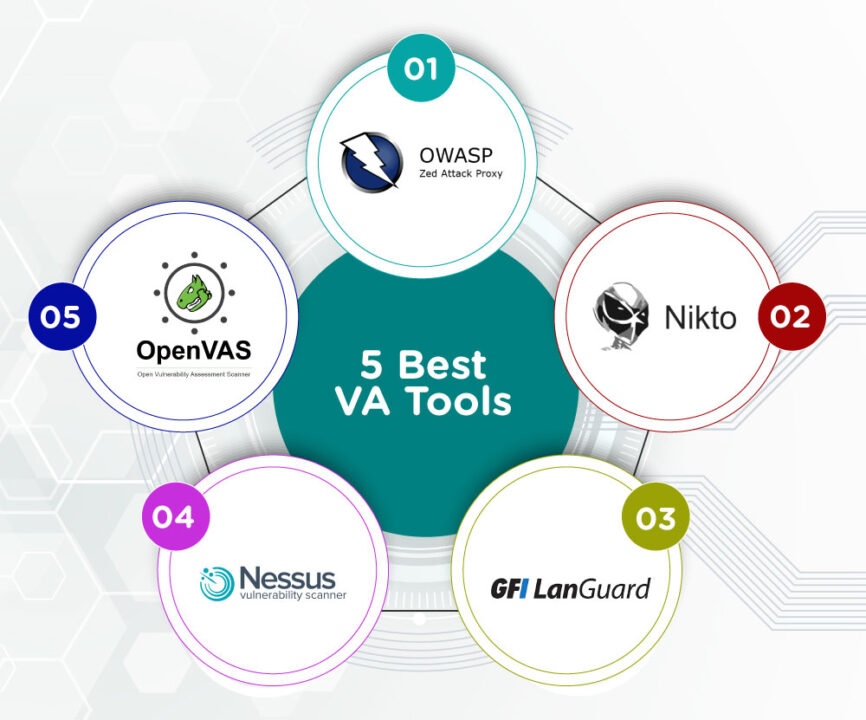
1 OWASP ZAP (Zed Attack Proxy)
It's an open-source penetration testing tool that helps AppSec experts accurately identify known and undiscovered cyberthreats. With its broad range of features, it is mostly utilized for online applications and aids in the rapid identification of various cyberthreats. They include:
- Carrying out passive web request scanning
- using the use of a dictionary list to scan files and directories on the server side
- Using an advanced crawler to correctly understand the site's structure and retrieve any dubious links and URLs
- Controlling all online requests sent and received between browsers and web applications
Because of these features, the OWASP ZAP tool is an excellent tool for identifying some of the most harmful online threats, including SQL injection, XSS, compromised authentication, exposed sensitive data, and more.
2 Nikto
It is also known as Nikto2. It is a web server scanner that is free to use and open source. It searches for outdated web server software and vulnerabilities on web servers, including malicious files and programs. Additionally, it scans for faults in server settings and any potential vulnerabilities they may have caused.
Key attributes:
- It is free to use.
- It is capable of scanning any web server, including Apache, Nginx, Lighttpd, Litespeed, and others.
- Checks for configuration problems, such open index directories
3 GFI LanGuard
GFI LanGuard enables you to examine, identify, evaluate, and fix security flaws in your network and linked devices. The tool supplies a comprehensive network overview and helps with simple security maintenance.
Main important features:
- Patch management for web browsers, operating systems, and third-party programs
- Find weaknesses before hackers use Web-based reporting
- Monitor the most recent security flaws and unreleased patches.
- Connects to external security applications
4 Nessus Professional
Nessus Professional, the most popular vulnerability assessment tool on the market, helps you minimize the attack surface of your company and maintain compliance. Among the many functions offered by the Nessus vulnerability scanner are malware detection, target profiling, configuration auditing, sensitive data finding, and fast asset discovery.
A program called Nessus checks key infrastructure, databases, web servers, hypervisors, OS systems, network devices, and next-generation firewalls for security flaws and noncompliance. It supports more technologies than competing solutions.
Nessus Professional sets the benchmark for vulnerability scanning speed and accuracy thanks to the world's biggest continually updated library of vulnerability and configuration tests and Tenable's knowledgeable vulnerability research team.
5 OpenVAS
It is an essential tool for identifying computer system vulnerabilities. Networks, systems, and applications are scanned for possible security threats using a continuously updated database of known vulnerabilities.
The application gives system administrators and security experts comprehensive details about every danger it has identified, assisting them in comprehending the nature of the risk and possible alternatives. Because OpenVAS is open-source, adaptable, and available to a large user base, it continues to lead the way in vulnerability assessment. Following are the features of OpenVAS:
- Thorough Vulnerability Analysis
- Merging with Other Tools
- Verified Scanning
- Guidelines for Remediation
Vulnerability Assessment Techniques
Common techniques for carrying out a vulnerability assessment include:
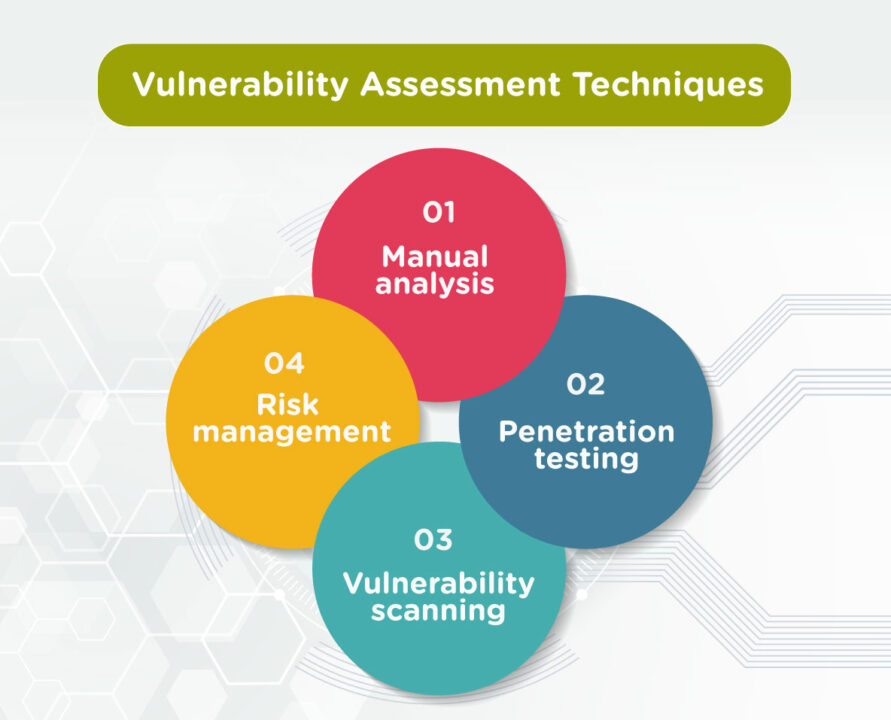
1 Manual analysis
To find such vulnerabilities, security researchers manually examine configuration files, log files, and system code. Automated tests, including vulnerability scanning and penetration testing, are frequently combined with manual analysis.
2 Penetration testing
Pen testing, another name for penetration testing, is a kind of security test that mimics an assault on a system or application. Using an offensive or active collection of tools, ethical hackers often take on the role of a criminal in order to find vulnerabilities.
It is possible to do pen tests automatically or manually. Ethical hackers do manual penetration testing to try to take advantage of weaknesses in applications and systems. Utilizing software tools that mimic an attack, automated penetration testing is carried out.
3 Vulnerability scanning
One kind of automated test that looks for known flaws in systems and apps is vulnerability scanning. Both external and internal systems may be evaluated with vulnerability scanners.
A vulnerability signature database is used by scanners. When a vulnerability scanning tool detects a possible vulnerability, it generates a vulnerability scanning report that describes the issue's severity and possible remedies.
4 Risk management
Understanding and reducing risks to an organization's internal systems, including its IT, is the practice of risk management. It is an active security strategy that assists companies in recognizing and lessening the effects of possible inbound and outbound threats from both the inside and the outside.
The 4 steps of risk management are given below:
- Determine: Determine any hazards to the organization.
- Evaluate: Evaluate each risk's probability and consequences.
- Mitigate: Risks may be reduced by implementing controls like security rules and procedures.
- Monitor: Keep an eye on how well controls are working.
Strengthening Cybersecurity Through Vulnerability Assessments!
To maintain strong cybersecurity, vulnerability assessment is a crucial procedure. Organizations may proactively manage their security risks, guarantee compliance, and defend their systems against possible threats by utilizing cutting-edge technologies and procedures. To remain ahead of the always changing threat landscape, regular evaluations are essential.
Through this blog post, we made the best effort to explain the concept of vulnerability assessment; we hope, as a reader, you find it helpful. To bring more engaging and insight-giving content, visit our blog page, WisdomPlexus.
Recommended For You:
Top 10 Vulnerability Assessment Best Practices: You Should Be Aware About