Emails are the widely used method of business communications. But like other technology, it too is vulnerable to various attacks.
Spoofing is one of many attacks that email is vulnerable to. Within this, an email is sent from a forged sending address.
Attackers use this type of technique to exploit email filters by making users believe that their message is from someone they probably know or can trust.
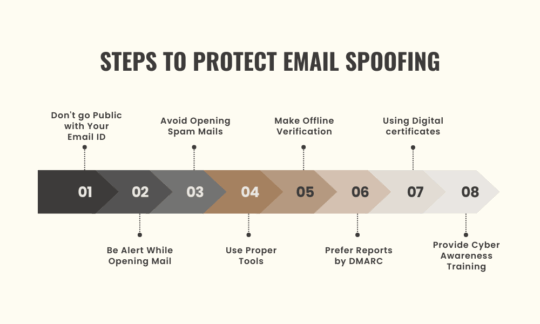
However, a user can protect or stop its domain from being a victim of email spoofing by going through below mentioned steps.
Below mentioned are some of the steps that guide users on how to protect email spoofing.
Email-id is one of your essential digital contact addresses.
Keeping it public gives hackers easy access to reach your system,, where all of your important data might be preserved.
This can prove to be a significant security breach in case a user is using a weak password.
Even an automated filter might not be able to mark some risky emails as spam.
Users are advised to be alert whenever a mail drops in their inbox.
Users should adequately check such mails' subject lines as they may contain free offers or discount offers.
Moreover, users should check the contents of such emails and refrain from downloading any banner or links provided in the content.
Also Read: 7 Best Email encryption solutions: You should be aware about
Users should avoid opening spam emails as, most of the time, hackers have intentionally sent these to gain access to your information.
Even automated email filter sometimes marks genuine mails as spam mails, but users are still advised to check the content to make sure about the spam's email.
Anti-spamming and anti-virus can assist users in filtering or scanning the mails for the virus.
Such tools keep users safe from infected mails by quarantining them.
Always prefer confirming the authenticity of mails by offline mode if any contact has been given.
Doing so will make sure that the sender is genuine and users can in nearby future mark it as safe to avoid any confusion.
Users stop email spoofing from the domain by opting for DMARC (Domain-based Message Authentication, Reporting, and Conformance).
DMARC is a protocol that uses SPF (Sender Policy Framework) and DKIM (Domain Key Identified Mails)
DMARC makes it easy for ISP (Internet Service Providers) to protect users from infected email practices.
If an email is not SPF or DKIM authenticated, DMARC here provides users the option to send these emails to the junk folder.
This makes detecting spam and phishing emails easy for ISP’s.
Using digital certificates like S/MIME (secure multipurpose internet mail extension) will provide confidence and trust in the emails sent from the user’s end and thus keep their information safe.
Suppose it’s your employees that handle the majority of your business email communication. In that case, it is thus in the best of your interest to update their knowledge with the latest tricks of handling such situations.
They can be trained to look out for such signs while dealing with infected mails
• Check the grammar, spelling, and language of such emails.
• Check if the content is eagerly asking you to click any links.
• Check for any mismatches in the content of the emails.
Spam and Phishing are commonly used methods to drive information from your systems.
Spam
Spam messages are usually commercially focused emails like advertisements, discount coupons, etc. wherein a user is tricked into clicking it.
Such spam messages are of two types:
• Intentional: Here a user is asked by spammers to click on the message with the intention of committing fraud.
• Unintentional: Here without the awareness of the user bulk emails are sent from the user's infected system.
Phishing
In a phishing attack, the spammer's main motive is to fetch the user's personal information like Date of birth, email address, social security number, etc.
Phishing messages seem legitimate at first glance, asking users to click the link in the message to update or review your account.
Such messages tend to fetch out the personal information of users.
In such cases, a user is advised to be alert and check the below-mentioned points to verify the authenticity of such mails
• Check the URL
• Check for the hyperlinks
• Check for the Lock symbol on the page.
Spoofing
Spoofing messages are a combination of spam and phishing attacks, but the sender information is altered with the fake address.
Usually, in such messages, spammers update commands in header format and alter the message information, like the sending address, so that a user believes that a known source has sent the message.
Conclusion
Email spoofing might seem like a past thing, but with the world and technology changing rapidly, hackers update themselves accordingly. The steps mentioned above will surely help users identify malicious emails and keep you and your personal information safe.
Also Read: 8 Best Practices for Network Monitoring