Computer systems & networks have reached a greater level of complexity than ever before. No organization wants its network infra to become the target of malicious exploiters.
So, if you suspect your site is vulnerable, it is necessary to take precautionary measures.
Scanning your networking system with vulnerability assessment tools, thus becomes a must. In case you're unsure about opting for these tools, you can start with an open-source tool (which is mostly freely).
Vulnerability Management in a Nutshell
The method of recognizing and categorizing security breaches in network infrastructure (be it hardware or software systems) is known as vulnerability analysis.
Often found in operating systems or software running on your servers, security risk can be anywhere. If left unsupervised, these vulnerabilities can be used by malicious exploiters.
To assess or evaluate the security of any network, the following six steps must be focused on:
-
- Track the systems, data, and applications that are exercised during business practice.
- Investigate invisible data sources that can allow easy entry into protected information.
- Monitor all existing security measures that are already in place.
- Classify the physical and virtual servers that run the required business applications.
After vulnerabilities are evaluated, it is time to decide how to address and fix them. It is best to replace the software with any other software of similar capabilities, in case any vulnerability is observed.
In other circumstances, fixing vulnerabilities is as simple as applying a patch from the software publisher or upgrading to the latest version. Many vulnerability scanning tools determine the fixes available for the vulnerabilities found.
There are many things to consider when selecting a vulnerability scanning tool. One of the most important aspects of these tools is the variety of devices that it can check.
Below mentioned are some of the top open-source vulnerability scanner tools:
Arachni is a widely admired open source web scanner, with a high-performance Ruby framework. It is used to assess vulnerabilities and accuracy for modern web application technologies.
It is versatile and supports all significant operating systems such as Linux, Mac, and Windows.
Key Features:
-
- Multiple deployment options.
- An abundance of security checks including XSS, SQL injection, code injection and NoSQL injection
- Integrated browser environment and provides support for DOM/JavaScript/AJAX/HTML5
- Highly detailed and well-structured reports.
sqlmap is an open-source penetration testing tool that comes with a powerful detection engine. It automates the method of detecting or assessing vulnerabilities.
If you have a Python interpreter, this tool can be used on any operating system as it is developed in Python. From finding flaws to exploiting them, it has niche features for penetration testers.
Key Features:
-
- Capacity to enumerate automatically database information
- Automatic recognition of password hash formats
- Complete assistance for six SQL injection techniques
- Exploits SQL injection vulnerabilities
- Supports the following databases: MySQL, SAP MaxDB, Oracle, IBM DB2, PostgreSQL, Microsoft Access, Microsoft SQL Server, SQLite, Firebird, and Sybase.
Also Read: List of 11 Patch Management Best Practices: You Should Follow
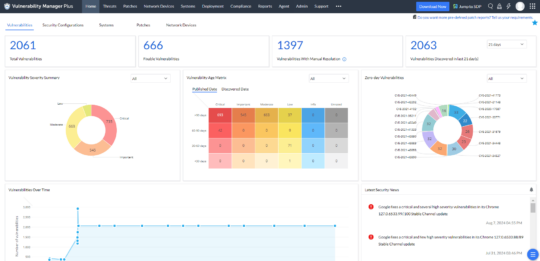
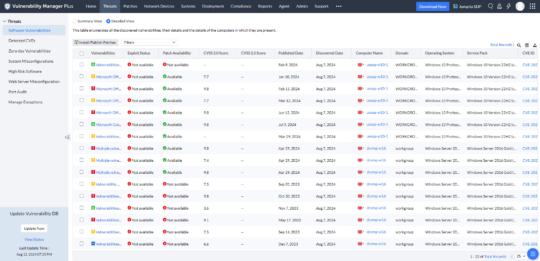
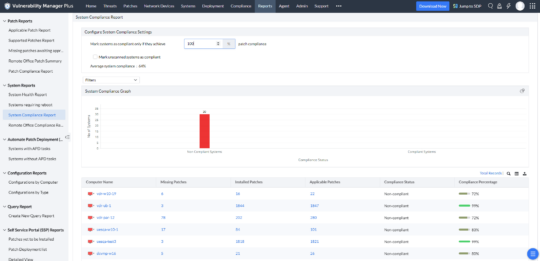
Vulnerability Manager Plus is a comprehensive vulnerability management and remediation solution that delivers 360-degree security monitoring to safeguard businesses from emerging threats. The end-to-end vulnerability management tool enables IT admins to conduct thorough security posture analysis, including zero-day vulnerability assessments, third-party application vulnerability detection, and remediation of risky security misconfigurations across endpoints. The solution offers extensive network device vulnerability management, including port and software audits, helping organizations maintain a strong security baseline.
To counter zero-day threats, Vulnerability Manager Plus mitigates risks by deploying scripts that enforce secure configurations, modify registry values, and close vulnerable ports, reducing the attack surface before official patches become available. It also features CIS compliance auditing to benchmark system configurations against security best practices. Additionally, the tool monitors web server misconfigurations, addressing risks related to HTTP headers, SSL/TLS, DDoS vulnerabilities, and cross-site scripting (XSS). Its system quarantine capabilities enable organizations to isolate compromised endpoints, prevent lateral threat movement, and minimize security risks.
Key Features:
-
- Advanced vulnerability assessment
- Compliance with the 75+ set security benchmarks.
- Customizable patch management
- Optimized security configuration
- Web server security enforcement
- High-risk software audit
- Zero-day vulnerability mitigation
- Network device vulnerability identification
Considered as one of the most popular penetration testing tools, Nikto is an Open Source (GPL) web scanner. It is used to test a web server in the shortest possible time and provide comprehensive reports in plain text, XML, HTML, NBE or CSV.
It also audits for server configuration items such as the existence of various index files, HTTP server options, & seeks to determine installed web servers and software.
Key Features:
-
- Scans various protocols like HTTP, HTTPS and HTTPD.
- Apache and CGIWrap username enumeration.
- Scans multiple ports on a particular server.
- Checks for outdated server components.
- SSL and complete HTTP proxy Support.
- Easily updated via command line.
Wapiti is a command-line application that audits web application for critical vulnerabilities, proving that they are real and not false positives.
This tool performs black-box scans i.e. instead of studying the source code, it will scan the pages of the deployed web application, on the lookout for scripts and forms where it can inject data.
It can detect vulnerabilities such as file disclosure, file inclusion, XSS, CRLF Injection, backup files disclosure, and many others.
Key Features:
-
- Supports GET and POST HTTP method, HTTP, HTTPS, and SOCKS5 proxies.
- Easy to activate or deactivate attack modules.
- Different levels of verbosity.
- Generates vulnerability reports in various formats.
- Aware of HTML5.
Based on GUI, Vega is a complete automated assessment tool that runs on Linux, OS X, and Windows. Given the user credentials, Vega can automatically log into websites.
It can help you detect and exploit vulnerabilities such as cross-site scripting, header injection, directory listing, file inclusion, shell injection, SQL injection, & more.
Key Features:
-
- Automated, manual, & hybrid security testing.
- Easy to create new attack modules using the rich API.
- Well-designed graphical user-interface.
- Includes a website crawler powering its automated scanner.
Also Read: Top 10 Vulnerability Assessment Best Practices: You Should Be Aware About