Security in cloud technology in recent times has failed to live pace to expectations. Reducing the vulnerability of possible cyber-attacks by adopting these five cloud security strategies with a plan can greatly reduce risk.
Building a robust strategy will help avoid common loopholes, the inclusion of all key stakeholders, identifying vulnerabilities, investing in training employees along using a layered cloud security approach will surely protect the system.
Develop a strategy for cloud security:
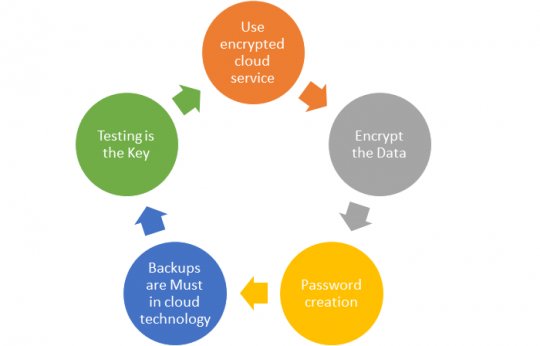
Some cloud technology service providers provide local encryption along with data storage and backup, thereby solving safety issues and ensuring that neither the service provider nor the admin will have access to your private information. The breakdown to this is to divide your data on the level of privacy it needs thus defining the level of protection needed for it, thus maintaining the balance between costs, incurred time, and the amount spent.
The easiest way is to zip the file, encrypt it with a password as no one will be able to access it without knowing one, and then move it to the cloud. Thus providing protection and making it more reliable, in case you want to opt for more cloud security the data can be encrypted using TrueCrypt – encryption software in cloud technology which is an open-source encryption program to keep all your private files protected with the password.
Even though you are well aware of this, hackers can crack most passwords in a few seconds. Creating double passwords may result in all login details landing up in your email account, as you may forget the credentials numerous times. Hence, a simple trick to strengthen passwords is to use core words in the structure and add numerics.
Taking backup seems to be obvious but many small businesses fail to do this. They are necessary for complying with Cloud security requirements, as they prove to be a safety net in your long-term business plan.
Testing is the right way to check whether your cloud security team works appropriately or not for that purpose both internal and external testing needs to be done regularly. Also, you need to document these errors as they can be worked on and maintenance is required considering the future.
Conclusion
Exploring the vast field of cloud security and building a robust protection system are essential guidelines for organizations.
You may also like to Read: