What Is Mobile Security?
Mobile Security is referred to as securing mobile devices like laptops, smartphones, tablets, and other portable computing devices from vulnerabilities and threats associated with wireless computing.
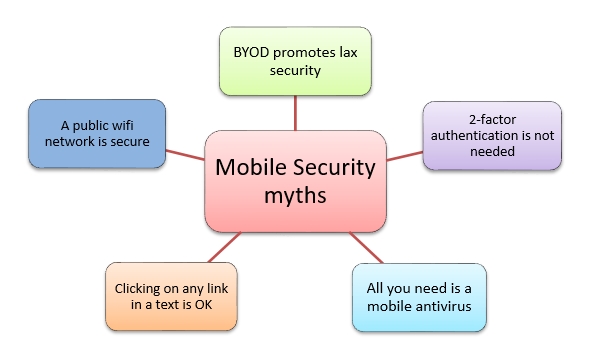
Mobile security also known as mobile device security, has become increasingly important in this era of mobile computing. Mobile security seeks to address the downside of this era i.e. Security gap. Here are five security myths about mobile devices :
-
- BYOD promotes loose Security practices
Businesses and their employees are profiting from device-sharing strategies. One of these trends called Bing your device (BYOD) is helping the latter. If an IT organization has firm guidelines to ensure that personal devices should be accepted in the BYOD program coupled with IT security practices and usage practices, then BYOD can be just as secure as mobile devices issued by enterprises. - Two-factor authentication is not needed for mobile devices
Two-factor authentication ensures security since most of the time the user ID and password are stored in your device, which is prone to be misplaced. It is therefore advisable to use an additional security sign-in code (e.g. name of the high school you attended) along with your user ID and password. - All you need is a Mobile Antivirus
The antivirus solutions for mobile devices are limited compared to PC antivirus solutions. They cannot use the same advanced detection techniques due to a mobile device’s limited battery life and performance. You might think you are protected against known viruses, but a new one might hit your device before an antidote has been developed. We need critical features like enterprise integration, application-based malware coverage, and firewall protection for mobile devices. - Clicking on any link in a text or WhatsApp message is OK
Scammers circulate fake offers through WhatsApp messages. Clicking these fake URLs may infect your mobile device with a virus. It might also take you to a fake login page that steals sensitive data like credit card numbers and passwords. - A public WiFi network can provide secure access
It is not very difficult for a cybercriminal to create a spoof public wifi network that can capture and store all your data including your personal and financial information. Employees on the move are continually using public wifi networks for their mobile devices. It is advisable for organizations to issue virtual private network (VPN) connections, which is a safer approach as compared to using open wifi networks.
- BYOD promotes loose Security practices
Also Read: