Organizations can effectively deliver better results when they are quick in responding.
High-traffic websites have to address millions of requests from both users and clients.
Too much traffic on a single server will affect the responsiveness in such situations.
Load balancer simply takes care of the network traffic, wherein it distributes the traffic among multiple servers to optimize system performance and to make sure that no individual servers are taking more loads.
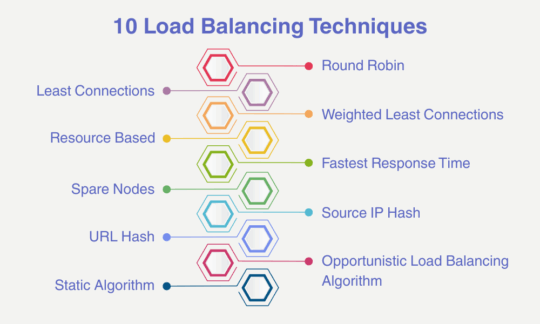
10 Load Balancing Techniques
Load balancing is dependent on certain techniques in order to optimize the performance of systems. Some of the load balancing techniques are discussed below:
Within this technique, client requests are forwarded to servers on a cyclic basis.
This means whenever there is any request from the client-side, the server that is first in the list will receive it and then the same request will be passed on to the second and then likewise till the last server.
When the request reaches the end server, the load balancer then repeats the processing of the new request again from the first server.
Since a load balancer assumes that the capacity of each server is same, it often results in inaccurate traffic distribution.
However, the same issue can be rectified through further weighted Round Robin and Dynamic Round Robin techniques.
Weighted Round Robin: Within a Weighted Round Robin technique, a weight is assigned for every server according to the weighting criteria set up by the administrator.
The commonly used criterion here is traffic-handling capacity.
Dynamic Round Robin: Weight here is assigned to servers based on real-time data received related to the server capacity.
Within the Least Connections technique, a load balancer looks specifically for those servers that are handling low active connections at the time of new requests.
Also Read: 8 Best Practices for Network Monitoring
Within the Weighted Least Connection technique, an administrator has predefined certain criteria.
Mostly, such criteria are traffic handling capacity.
An administrator assigns weight to servers on such criteria.
In Weighted Least Connection, decisions of distributing the traffic load is made on both the active and current connections of servers as well as on server capacity.
This technique is grouped into two categories:
Resource-based (Adaptive)
Within this technique, a load balancer is dependent on agents.
Agents are installed on application servers.
These agents further pass on the information related to the server availability, server status and resources.
The load balancer, in order to make decisions for distributing traffic, is dependent on agents for such kind of information.
Resource-based (SDN Adaptive)
Within this technique, information from layers 2, 3, 4, and 7 and an SDN (Software-defined networking) is collected and used for making better traffic distribution decisions.
It provides the load balancer with enhanced information related to server status, application status, applications running, the status of network infrastructure, etc.
Within this technique, proper tracking of nodes is done related to their responses for networks.
This helps in discovering new connections and routes, such as connections to servers having the quickest response time.
As the name suggests, it’s a spare node that is used whenever a particular server is not responding.
It exists in the cluster of servers and performs similar tasks to other servers.
However, it assists in the smooth functioning of the cluster whenever a particular server is not responding or is down.
It generates a unique hash key that is used for allocating a particular server to the client.
This key is generated by combining the source and destination IP addresses.
The benefit of this key is that it can be regenerated, and if there is a session breakout then the client can be directed to the same server that it was previously using.
It is the same as Source IP Hash but in this case, the hashing is done on the request URL.
The benefit of this technique is avoiding duplicate cache.
Within this technique, every node is allowed to keep busy.
The unfinished task is awarded to these nodes on a random basis.
This technique does not take into consideration the workload of these nodes.
It does not take into consideration the implementation time, because of which delays happen.
This technique is usually used in the case of systems that experience lower variations in terms of load.
Within this, the traffic is divided equally among servers.
The major glitch of this technique is that a load balancing task has to be created first and then only the load balancing tasks can be expected to work.
Conclusion
Load balancers assist enterprises in achieving optimal system performance through multiple techniques.
However, the task of load balancers is not only limited to minimizing the system failure but to boost the system performance as well.
Also Read:
What is the Importance of SNMP?
A Guide to Load Balancers: All You Need to Know