Many times your systems ask you to go for the updated versions.
This happens in order to fix the bugs or vulnerabilities within a program or product.
This happens because of the presence of patches.
Patches keep the machines updated and safe from other threats.
After an application is released, some of the flaws show up. Such flaws are addressed with the help of the patching process.
Let us discuss some of the questions related to patch management.
The patch can be defined as a piece of code that is created to fix any bugs or issues in the applications or software.
Patch management can further be defined as the process wherein a network of computers is kept updated and secured from any vulnerabilities by performing patch deployments.
The process can be automated at every stage in order to minimize the possibility of risks within an application.
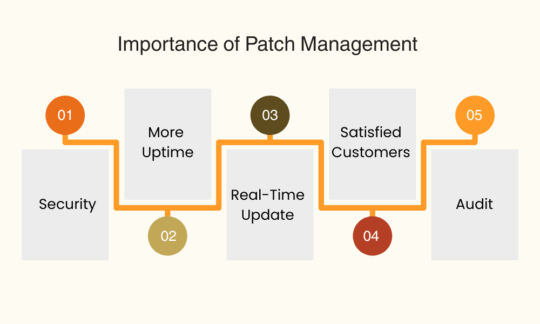
There are multiple reasons that support the importance of a patch management process. Some of the key points are discussed below:
• Security
Patch management assists users in fixing the bugs and vulnerabilities within their application or software.
This in turn assists organizations in keeping their costs low in terms of security.
Moreover, the patch management process assists users in keeping their applications safe from any futuristic vulnerabilities.
• More Uptime
More the downtime your applications have, the more damage it can bring to your business or applications.
With patch management be ready with updated versions in order to avoid any last-minute issues.
• Real-Time Update
Patch management provides real-time updates of your networks including endpoint devices and provides users with updates related to any vulnerabilities or missing security patches.
• Satisfied Customers
If your applications are being used by customers, their efficiency will ultimately provide a better experience to them.
If proper bugs are fixed, vulnerabilities or security loopholes are filled that will ultimately provide a better experience to end customers.
• Audit
Every application present on the network can be easily audited for its patches and users can thus receive reports on the health of the network as well as applications.
Also Read: List of 5 Open Source Vulnerability Scanner Tools
Some of the best practices for patch management are discussed as under:
Maintaining an updated software inventory will provide easy access to the information of every device type present on the network.
Users need to update their software inventory to evaluate the actual security standard of their organization.
An efficient visibility assists in making security plans thus every device needs to be incorporated into your asset list.
Researchers within vendor companies continuously evaluate the security of their applications and if any vulnerabilities are found within the process, patch codes are provided for the same.
Ignoring such updates from vendors can cost your company in terms of both goodwills as well as finance.
Thus, its advised to stay updated with the vendor side updates.
For patch management to be effective it is mandatory to categorize your systems.
The higher-risk systems or parts should be patched first.
This will save the high-priority assets from falling prey to any attacks and thus save users from any loss.
By categorizing your systems, you are ensuring that the patch management approach is ensured at every stage and every part of the system accordingly.
Always check for the compatibility of the patches with the platforms or environment you are using.
There may be patch codes that might work better on the windows platform but not on Mac, Linux, or Unix.
Similarly, there might be patch codes or updates that will work better on modern ERP but not on legacy systems.
Deployment of new updates needs to be done much quicker.
The average time to deploy patches still is considered to be 12 days.
This is mainly because of the data silos and not having better departmental communications.
The advantage of faster patch deployment is that a user will have fewer patches to assess as well as prioritize.
Moreover, a faster patch deployment protects your application or software from regular attacks.
Manual patching is often tedious.
An automated patching tool can perform patching best and more efficiently.
An automated patching tool can provide a better approach to databases.
While opting for an automated patching tool, users need to look for properties like automatic scanning, scheduled scanning, and downloading missing patches from vendor websites.
Automating the patching process reduces the workload for administrators thus promoting efficiency as well as productivity.
Generating reports can be tedious if done manually.
It should be automatic as report generation takes a lot of time.
The more time users invest in generating reports the less time they are left with patch updates.
The longer the security loopholes stay in the system, the disastrous it can be for the organization.
So, it is in the best interest of the users to continuously scan their systems for detecting such loopholes.
A bad patch can further worsen the application as it might damage the system parts and make it more vulnerable to attacks.
Testing patches before updating them assists users in ensuring their accurate and safe functioning.
Creating a backup before making any new move is a welcome step and also a standard procedure.
Back up of complete system should be done, so that in case of an unsuccessful event the least we will have is our system restored easily.
Always document the changes and communicate the newly implemented changes to staff as well as stakeholders.
Keeping a record of new implementations will minimize confusion.
Conclusion
With more and more cyberattacks happening, it is of utmost importance to update your system applications accordingly. Above mentioned best practices will assist in a smooth patch process and also assist in the minimization of risks.
Also Read: Top 10 Vulnerability Assessment Best Practices: You Should Be Aware About