Data is the new oil.
Data is mainly responsible for every decision that a company takes in order to improve its efficiency.
Thus it has to be kept secured.
One main technique in order to protect the data is data masking.
Within data masking, a fake but realistic version of the original data is created. The goal of such a process is to protect sensitive data.
The values of the data are changes but are kept in the same format so as to protect it from attacks or reverse-engineering attacks.
Let us answer some of the questions related to data masking.
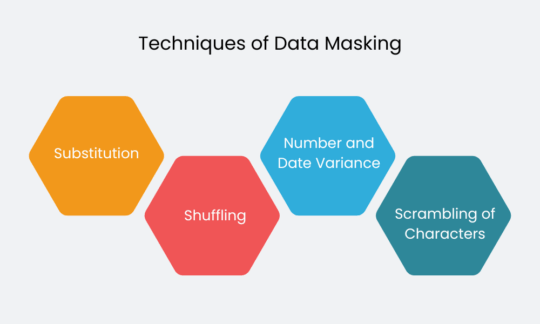
Given below are some of the techniques used in data masking:
Substitution
Here, the original data is substituted with the random data. The sole purpose here is to disguise the data.
Shuffling
Here in this technique, the method is the same as that of the substitute one, but the entities are shuffled in the same column randomly.
Number and Date Variance
This type of technique is mostly used in financial and data-driven datasets.
Here, in this type of technique, the same variance is applied in the creation of new data sets.
This though, doesn’t change the accuracy of the data sets whenever the masking is done.
Scrambling of Characters
Within this method, the numbers are randomly rearranged.
Being an irreversible process, it is difficult to obtain original data from the scrambled data.
Also Read: 7 Best Practices for Data Integration: You Should be aware of
What Are the Best Practices of Data Masking?
Discussed below are some of the best practices for data masking.
While opting for the data masking procedure, it is advised to chalk out the scope of the project.
By scope, we mean as to what department is to be brought under this procedure, which information has to be protected, who is authorized to see it.
It seems to be an easy process on paper, but due to the multiple lines of business and multiple departments, this process asks for more efforts.
Many businesses have many departments.
Majority of the time due to budget issues every department needs to implement its own data masking tool.
In such situations, organizations are advised to synchronize every data masking tool as well as the practices in order to avoid future confusion.
Algorithms need to be considered extremely sensitive and should be only given access to authorized users only.
Leaking of information about the algorithms being used can result in hacking of sensitive information.
Organizations should use such tools that transform the information in an irreversible format.
This means that the data that has been transformed cannot be reversed under any circumstances.
Environments such as testing or development have higher chances of data breaches.
Organizations should make sure to protect the data from these environments.
Execution of data masking is not enough.
Organizations should be equipped with certain approaches in order to identify sensitive information.
Moreover, a detailed data audit needs to be done in order to ensure that all these protective measures are working.
Data available with the organizations needs to be classified properly in order to protect them.
Classification of data should be done as under:
High sensitive data, that will include credit card numbers, passport numbers, last names, addresses etc.
Moderate sensitive data, that will include first names, dates of birth, financial records etc.
This classification of data will give an idea to the organization as t which particular set f data needs to be given priority.
Select the applications that are using private data.
Organizations should opt for such applications that are storing a larger amount of sensitive data and are used by maximum users.
Data in the organizations keep on changing quickly.
Organizations need to make sure that the data received is being properly masked within set time and is being delivered through secured channels.
Last but not the least, test the application that you have selected for data masking on different parameters in order to have a clear understanding of its working.
Test the application with both maximum as well as a minimum number of masks.
Conclusion
A data breach not only costs the company in a financial manner but also affects its market goodwill.
Above mentioned steps will assist organizations in the implementation of the best data masking strategies and will keep them secured from any future hack issues.
Also Read: Data loss prevention techniques: You should follow.