Communicating in a professional business environment is mostly done by Emails.
It is one of the essential methods of communication in the business world.
But it carries a drawback with it.
Emails are prone to cyber-attacks like hacking or phishing.
Thus, email encryption is needed to ensure the safety of emails over a network from the source to the destination address.
Let us discuss some of the Email encryption solutions below.
Best Email Encryption Software
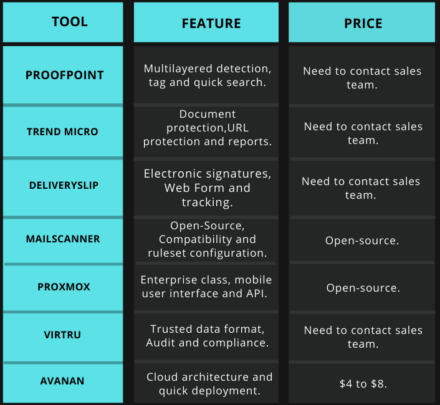
Proofpoint assists users in securing their emails through machine learning and multilayer detection techniques.
It can be deployed both on the cloud level and on-premise.
It assists users in keeping their emails safe by detecting and blocking phishing and imposter emails.
Key Features
• Multilayered Detection: Analyses the contents and the reputation of the sender and blocks such emails from entering your system.
• Tag: Users can tag any suspicious emails for the end customer to make them aware of the reputation of such suspicious emails.
• Quick Search: It helps users search any type of data from the email logs and provides them with a tracking system as to where the email has been sent and received.
Price: Need to contact the sales team for pricing.
Reviews:
As mentioned in the review section of g2.
A sales manager of SME finds it extremely useful in eliminating the space issue by deleting spam mails and only allowing the important ones to stay in the inbox.
Also Read: 8 steps to prevent your emails from spoofing
Trend Micro email security uses techniques like e machine learning, sandbox analysis, data loss prevention (DLP) to stop email threats.
Trend Micro email security helps users have central visibility of threats by connecting users with other Trend Micro security layers.
It is efficient for on-premise solutions and protects email sent from platforms like Microsoft Exchange, Microsoft Office 365, Gmail.
Key Features
• Protects Your Documents: If any of the documents is infected with any malicious virus, Trend Micro email security with static and heuristic logic detects it and examines it.
• URL Protection: If an email contains any malicious URL, it will block and recheck it when users click it.
• Reports: Generate reports for assessment.
Price: After the trial period of 30 days’ ends, users need to contact sales team.
As mentioned in the review section of the Gartner.
An information security specialist finds the installment of TrendMicro email security easy to deploy and considers it quite futuristic in communication
DeliverySlip works accordingly with the user’s email client and doesn’t bypass users' existing security filters and appliances.
Users have the privilege here to secure files of maximum or unlimited size.
This thus removes the barriers of inbox size restrictions.
Key Features
• Supports Electronic Signatures: Assists users in determining the authenticity of the documents. Moreover, it supports wet signatures, stamp signatures, etc.
• Web Form Protection: It extends its security features to web forms, which helps the user collect data safely.
• Tracking: Provides users with notification assistance and keep track of messages right from receiving, reading, or forwarded.
Price: Need to contact sales team for pricing.
As mentioned in the review section of g2.
Nicholas R, who happens to be the organization manager of consumer service department in a mid-market size company finds DeliverySlip quite useful in encrypting the emails and upholding their email security policies and also appreciates it being operable on a cloud platform wherein security filters are provided for safety of mails.
MailScanner, is an open-source email security system.
Being an open-source platform, it has continuously been upgraded by the computer security world's best minds.
It is installed as a gateway or is integrated with mail gateways.
It also supports the spam detection platform Spamassassin, which is considered the best in detecting spam.
• Open-Source: Being open-source, it is entirely free to download and is continuously upgraded by experts.
• Compatibility: MailScanner is compatible with almost every email transport software like Sendmail, Postfix, Exim, Zmailer, and Qmail.
• Supports Ruleset Configuration: Ruleset configuration assists users in selectively applying the configurations based on pre-selected configurations.
Price: It is an Open-source tool so it can be used for free.
Review:
Reviews for MailScanner are not available as of now.
Proxmox mail gateway is an open-source email security platform that protects the user's mail server against any threats.
It’s easy use web interface makes it easy for IT teams to control all incoming and outgoing emails.
Organizations of any size can use it.
It is deployed between the firewall and the internal mail server and can even be controlled from a single platform.
Key Features
• Enterprise Class Email Security Solution: Provides users with the benefits like scanning of incoming and outgoing mails, easy integration with existing mail servers etc.
• Mobile User Interface: Users can check the status of their sent messages through mobile devices.
• API: Allows easy integrations with any third-party management tools.
Price: Being Open-source it is free to use.
Review:
As mentioned in the review section of g2.
One of the customers finds it easy to use because it is a free email encryption tool.
Moreover, they find it quite easy to deploy it from an ISO TOO.
They find it quite good as it uses open-source hypervisors instead of closed source hypervisors.
Virtru provides end-to-end encryptions and advanced controls for emails and email attachments.
It can be easily integrated with email gateways like Gmail and outlook.
Key Features:
• No Third Party Access: With the help of interoperable standard Trusted Data Format (TDF), it provides controlling access only to the intended recipients.
• Audit: Granular audits assist users in finding out the content that is being shared and if the users intend to revoke the access, they can easily do that.
• Compliance: Provides audit reports if users are to protect PII, HIPAA, FERPA, GDPR, CCPA like regulations.
Price: Need to contact the sales team for pricing.
Review:
As mentioned in the review section of g2.
Melanie F, who happens to be a program support assistant in a government administration department finds it quite useful for mail encryption.
Its user-friendly step by step approach assist users in using mails and also opening of protected mails.
Avanan is another email encrypting tool.
It is used to secure cloud emails and collaborated platforms.
Key Features
• Cloud Supportive Architecture: Since Avanan is deployed in clouds connects to the user’s environment after users existing security but before the inbox.
• Quick Deployment: Easy to deploy like any other application in a few clicks.
• Complete security: Designed specifically for cloud platforms, it scans and catches the threat in other connected cloud applications too.
Avanan has rolled out three of its plans as discussed under:
• Advanced Anti-Phishing: Users are charged $4 per user per month under this plan. Other benefits under this plan include SmartPhish Anti-Phishing, Account Takeover Protection, Configuration Security, URL Clicktime Protection, Policy Enforcement, and Shadow IT
• Complete Malware: Users are charged $5 per user under this plan and benefits in it include all those of Advanced anti-phishing plans with malware sandboxing.
• Full-Suite Protection: Users are charged $8 under this plan and benefits include those of advanced anti-phasing plan, complete malware and data loss prevention.
Review:
As mentioned in the review section of Gartner.
Users found Avanan very impressive when it came to securing their office 365 from phishing attacks
Conclusion
Since the majority of business communications happen through emails, these are easily targeted by hackers or attackers for doing any harm to a business. The above-mentioned tool will assist you in setting an efficient email encryption strategy.
Also Read: Top 8 Self-Hosted Password Managers