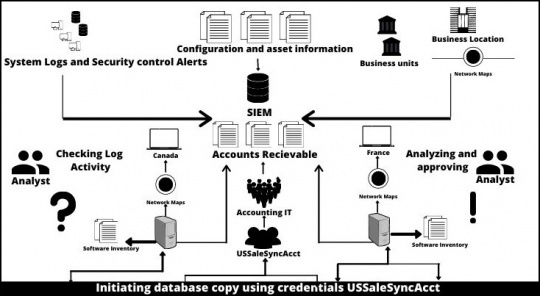
Security and information management (SIEM) is a cybersecurity technique wherein the focus is kept on the security of IT networks.
SIEM solution safeguards your entire IT infrastructure by keeping a close watch and analyzing the resources within IT networks.
Information is collected from network devices like servers, domain controllers, and controllers.
SIEM stores this data and applies analytics to find threats and issue alerts to the organization.
Logs are responsible for recording events happening in any operating system.
Within SIEM, logs collect the data from installed devices, network devices as well as storage protocols.
Issues needing immediate attention are forwarded to the organization after event analysis.
In case data needs any further investigation, it is stored properly for the same. Such types of data could be historical data or metrics.
SIEM interprets the data based on how the devices have been categorized.
Because of this categorization of the devices, SIEM parsing engine is able to interpret the data accordingly.
Information such as log records generated by a particular device type, data elements present etc. are recorded.
Also Read: Top 11 Network Configuration Management Tools
Since data is collected from multiple devices, it has to be presented in a meaningful and structured manner.
The correlation function here helps to present the bigger picture of the data collected from multiple points.
Through this correlation activity, a user can access information like which user is connected, what device is being used, what errors were generated, etc.
Users receive updates related to any type of security breach in real-time.
This thus helps in timely as well as efficient tracking and elimination of the threat.
If there has been a security breach in a network, all of the relevant data is taken into consideration for providing instant assistance in tackling such threats.
SIEM dashboards help security analysts to understand the change in any data pattern easily.
Thus, a security analyst can easily detect any abnormalities happening within the network easily and quickly.
Because of SOAR (Security, Orchestration, Automation, and Response), any incident can be automatically responded to without being dependent on security analysts.
SIEM reporting tool allows the generation of different reports for other administrators to minimize any confusion related to their report work.
SIEM generates reports efficiently as it saves every log information in database tables.
Data is, first of all, collected to perform further analysis.
SIEM collects data from multiple devices, including network protocols, host systems, antivirus filters, etc.
Data is often collected through the help of agents that assist in data collection related to event logs from enterprise systems.
After the collection of the data, it has to be stored for further investigations.
Traditional SIEM solutions use RDBMS storage.
Modern SIEM for data storage has shifted to distributed, horizontally scalable architecture and storage setups.
Data enrichment adds value to the information.
Within data enrichment, data is stored with its real identity, geolocation, and threat intelligence that could further prove to be of assistance in threat investigations.
This assists SIEM in exploring more while investigating any threats in the organization.
Data has to be stored in multiple formats for further assessments.
SIEM platforms usually store data overtime in two formats:
Tiered: It simply means collected data under different types are stored in different storages.
Such data is recently collected data.
This data is stored in a storage media that provides maximum throughput rates for better performances.
Archived: Such type of data is stored at archived locations as there is a lesser chance of using such data.
To derive a better conclusion out of the data, multiple techniques are used by SIEM platforms.
Traditional SIEM was used to find anomalies within data to drive relations among various data and use signature-based alerts.
But such techniques showed preliminary results that were too much distracted from the genuine ones.
This resulted in time wastage.
Modern SIEM uses techniques like machine learning and advanced analytical methods to zero in on the threats.
Another such method that modern SIEM platforms use is User and Entity Behavioural Analytics (UEBA).
Within threat investigation and its elimination, a SIEM platform usually depends on the SOAR technique solution.
SOAR provides an automation approach to deal with threats.
A SOAR solution helps analysts with the records that had been previously collected for threats, as to how was that particular threat eliminated, what were the steps are taken, whether the threat was real or fake.
With the integration of SOAR techniques, SIEM can deliver better results.
Moreover, SIEM solutions allow users to centralized solutions both for cloud and on-premise infrastructure.
Because of this, the automation technology SOAR could be used for monitoring security incidents across all connections.
Complete details related to connected devices and user behavior could be derived within the network.
It also gives users the immunity to pre-define the correlation rules. It will ease up security analysts' job as further security checks will happen on these pre-defined rules.
An efficient SIEM solution will provide real-time compliance reports on PCI-DSS, GDPR, HIPPA, SOX.
Data collected through SIEM platforms have to be in accordance with compliance standards.
The data that gets collected by SIEM is also checked for compliance standards.
Because of its automated reports generation and compliance verifying standards, it is the most sought out security solutions.
Moreover, with particular Add-Ons, it provides users with automated compliance with satisfactory reports.
Concluding SIEM Architecture:
Merely having a SIEM solution is not enough to protect your organization from threats.
Continuous monitoring has to be done, and compliance standards have to be followed while collecting data. Moreover, SIEM solutions, too, need to be maintained properly for them to perform efficiently.
Also Read: Endpoint Security vs. Network Security: Comparing the Two