Business operations have evolved with the emergence of advanced methods and tools. The use of mobile phones for organizational productivity is a key practice in recent times that offers high flexibility to employees. However, such trends raise significant security risks.
Mobile device management (MDM) is one of the most impactful techniques for securing mobile devices utilized for corporate purposes. According to reports, more than 1.8 million cyber threats take place against mobile users every month. It includes users for organizational purposes as well.
In 2024, more than 64% of businesses expressed their concern regarding increased security threats against mobile endpoints, contributing to the requirement of a robust security framework for important company devices like MDM.
In this blog, we shall learn about MDM, its importance, best practices, and more. Let's dive in...
What is Mobile Device Management (MDM)?
Mobile device management is a method to monitor and protect mobile security. It is chiefly adopted by organizations to analyze and safeguard applications within the endpoints, such as their employees' mobiles and tablets. The technique is applicable to both company-owned devices and personal devices of the workforce that they utilize for organizational purposes.
MDM's objective is to monitor corporate data while protecting it from vulnerabilities. The IT department or administrator usually handles such activities through specific tools, policies, guidelines, and configurations. MDM tools are principal elements of enterprise mobility management (EMM) and unified endpoint management (UEM). The process initiates identity and access management (IAM), mobile application management (MAM), file syncing, and sharing.
Though mobile usage in the corporate setting commenced at the beginning of the 2000s, the significance of MDM increased when the bring-your-own-device or BYOD framework received prominence. Under BYOD policy, the workforce of a company is allowed to use their personal devices to execute company responsibilities. Such an approach bears major security risks, due to which MDM tools are implemented.
Understanding the Process of MDM:
Mobile device management depends on two crucial aspects- the MDM server and the MDM agent. The former looks after the management, configuration, and enforcement of policies while operating within the organizational data center. On the other hand, the MDM agent integrates these policies into the devices, securing mobile endpoints. The policies and configuration methods may differ for organization-owned devices and gadgets under the BYOD policy.
After configuration and implementation, the policies are enforced on the applications and software installed in a device using APIs. In short, MDM uses a dedicated server and software to not only safeguard applications within a device but also manage the entire device inventory. The primary tactics it adopts for security purposes are identity-based access, GPS tracking, VPN integration, and token or password-based authentication.
Importance of Mobile Device Management in Modern Businesses:
Increasing cyberattacks against mobile devices and tech-enabled businesses have been a major reason for the enhanced adoption of MDM. Recent business phenomena such as remote work culture and flexible working hours boosted the usage of mobiles and tablets for organizational activities.
However, such devices became easy targets for cyber attackers. Insider attacks also soared, creating notable challenges for companies, including data breaches and financial loss. Lack of device authority and strong security parameters are two notable reasons for these risks. Mobile device management addresses all these issues, limiting the possibilities of attacks against organizational data and devices. Below are the distinguished advantages of MDM in modern business settings-
Advanced Security:
The usage of mobiles and tablets for organizational responsibilities is the reason for notable security weaknesses, allowing attackers to easily break into devices and steal confidential data. By implementing robust policies and access management tactics, MDM restricts cybersecurity risks against mobile endpoints. Alongside that, the process also allows mobile devices to stay compliant with data protection regulations around the globe, including GDPR, CCPA, and HIPAA.
Increased Control:
MDM enables higher control over corporate devices owned by a company and the workforce. One of the key reasons for increased threats against mobiles is the low visibility of employee activities on business assets. MDM enables enhanced visibility alongside control, empowering businesses to track functionalities at the employees' end even while operating remotely.
Limited Costs:
Mobile device management is comparatively cheaper than other device tracking and cybersecurity tactics. Additionally, it eliminates the possibility of significant financial losses, limiting cyber threats.
Primary Features of MDM:
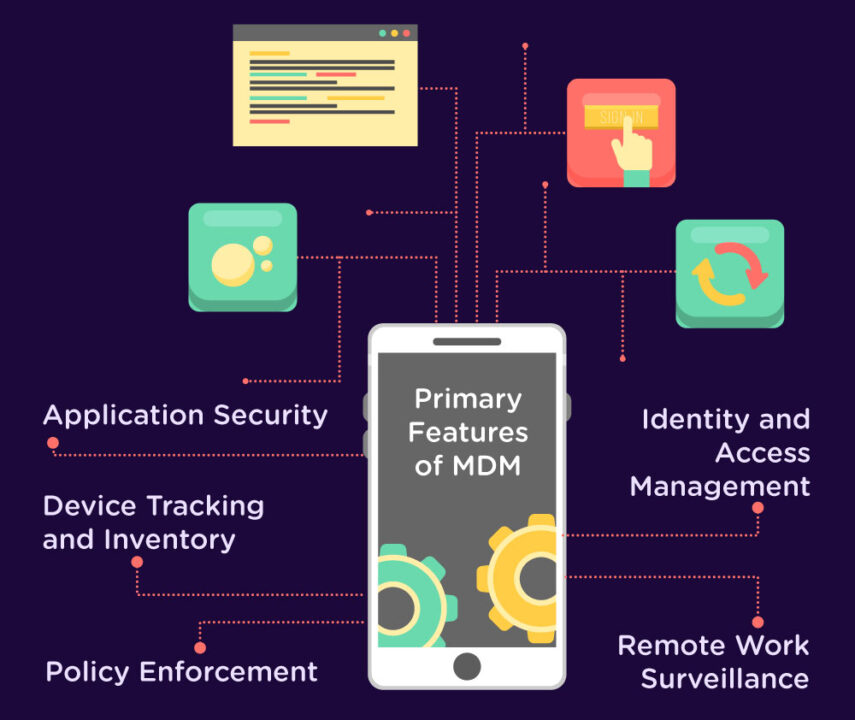
Application Security:
The applications under the MDM process are usually containerized, which enables advanced authentication and security measures. It further tracks data exchanges within devices, so when users try to access an application or share data, the MDM server will be able to monitor it, leaving no occasion for vulnerabilities.
Device Tracking and Inventory:
MDM utilizes GPS technology to detect and manage real-time device activities. The method allows companies to identify risks in devices and fix them quickly.
Policy Enforcement:
MDM depends on predefined policies that help in strengthening security. These policies assist devices in staying compliant with the cybersecurity guidelines of different regions.
Remote Work Surveillance:
When employees operate remotely using mobile endpoints, MDM strategies support organizations to monitor their activities and productivity.
Identity and Access Management:
MDM strategies use standard security tactics like IAM, ensuring authenticated data and application access only.
Exploring Mobile Device Management Best Practices:
#1 Automation in Updates and Task reports:
Since MDM strategies manage both in-office devices and BYOD, IT automation is necessary to make operations efficient and flexible. Automating application and device updates, alongside task report generation, enables agility, boosting productivity remarkably.
#2 Create Scalable Policies:
Build strong and scalable policies, enforcing them on mobile devices. Such an approach helps boost the efficiency of the security parameters within devices and troubleshoot weaknesses promptly.
#3 Implement Advanced Configuration:
Standard security configuration methods are crucial for mobile devices used for office work aside from setting passwords or encryption keys. The method also empowers devices to receive timely updates.
#4 MDM with BYOD:
Deploy MDM strategies for employees following the BYOD policy to enhance data and asset security. Alongside that, providing training to the employees under the BYOD policy is also essential to make them aware about how MDM infrastructure works.
#5 Integrate Suitable Tools:
Several cybersecurity-providing companies offer MDM services, safeguarding mobile endpoints and organizational data. Moreover, establishing an entire MDM structure can be complex for many companies. Hence, integrating such third-party facilities enables a stronger security framework.
Adopting Mobile Device Management Tactics for Secure Business Operation:
Mobile device management monitors and strengthens application management, data storage, content management, email supervision, remote control, security assessment, profile identification, asset management, and others. In a way, the process simplifies as well as secures the overall functionalities of mobile endpoints within the organization.
Therefore, MDM is unavoidable for modern businesses that have deployed mobile devices for work. Nevertheless, considering factors such as cost, usability, and compatibility is essential while looking for the appropriate service provider for mobile device management.
Stay aligned with the knowledge curve in the tech-enabled era with our informative blogs!
Also Read: Five Myths about Mobile Security




